Features, Scoring, and Technology
Overview
The E-HAWK API service provides real-time reputation, validation, and risk assessments for leads, sign-ups, registrations, account updates, and logins.
When an individual signs up for a service, fills out a form, updates their account information, or tries to complete a transaction on your web site, just embed our Vetting API to check the risk levels of the identity entering the data. Then pass the Risk Score and risk details onto your business systems and take the necessary actions.
Test Areas
Data supplied to the API is analyzed using a broad spectrum of tests incorporating big data, machine learning, and advanced analytics. The API groups results into rollup areas for IP, email, phone, location, domain, activity, geolocation, device, SSN, Tags, and community.
Each area runs many sub-tests as well as cross analysis between linked data (for example the IP and the location). When the analysis and tests are complete, the API returns a Risk Score as well as scores for each area and risk reasons found in a response JSON.
Our analysis includes hundreds of tests some of which include:
- IP traffic risk, bots, worms, proxies, TOR, blocklists, spam history, geolocation
- Email suspect, disposable, free, MX, reputation, history, age
- Domain registration, age, parked, for sale, blocklists, suspended, name servers, suspect content
- Phone line type, disconnected, association with fraud or multiple emails
- Names profanity, suspect, bogus
- Geo-location distances between data points, country risk factors, movement velocity
- Velocity and Uniqueness of data points, phonetic repeating,
- Device fingerprint reputation and activity
- Millions of community records added from customers who share fraudster information
and more. In addition, all scoring can be customized to meet your business risk tolerance levels.
How is the risk score calculated?
The score starts at zero. When our risk engine discovers good things, such as a clean IP, some positive points are added. When bad things are identified such as a history of spam or fraud, negative points are scored.
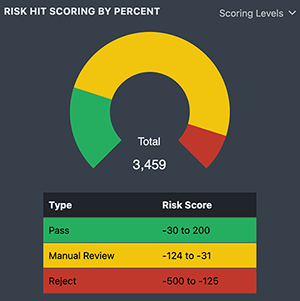
The API returns an overall Risk Score as well as scores for each tested area, such as email, IP, and device fingerprints. Most vets have some risk, but Risk Scores of -71 and below should be of concern and raise red flags. All scoring is customizable, so your scoring should be set to exceed your bad lead threshold. As a general guideline for risk levels, we also return Risk Type with the Risk Score.
| Type | Risk Score |
|---|---|
| Lowest Risk | 10+ or higher |
| Low Risk | 0 to 9+ |
| Some Risk | -1 to -15 |
| Medium Risk | -16 to -30 |
| High Risk | -31 to -70 |
| Very High Risk | -71 to -100 |
E-HAWK performs risk checks in real-time for each API call. In addition to returning a Risk Score, we also return risk hit details. As an example:
Score: -100
Type: Very High Risk
Disposable email
IP on blocklist
Domain 3 days old
4 Repeats
With these details, your company can take specific actions based on actual risk hits, not just a simple score. We also have an Alert system that will notify you when your user score changes, block listed or become high risk.
These default risk bands can be modified with custom names and score thresholds. As an example, a simple scoring band of Reject (-500 to -125), Manual Review (-124 to -31), and Pass (-30 to 200) can be created in the portal.
Fingerprinting
The Talon JavaScript creates a device Fingerprint for each API call. Using fingerprints makes it easier to tag bots, muti-signups, and other risk issues including device spoofing. The Portal tracks all fingerprints and links to the data details page so you can quickly view all API calls associated with a specific device.
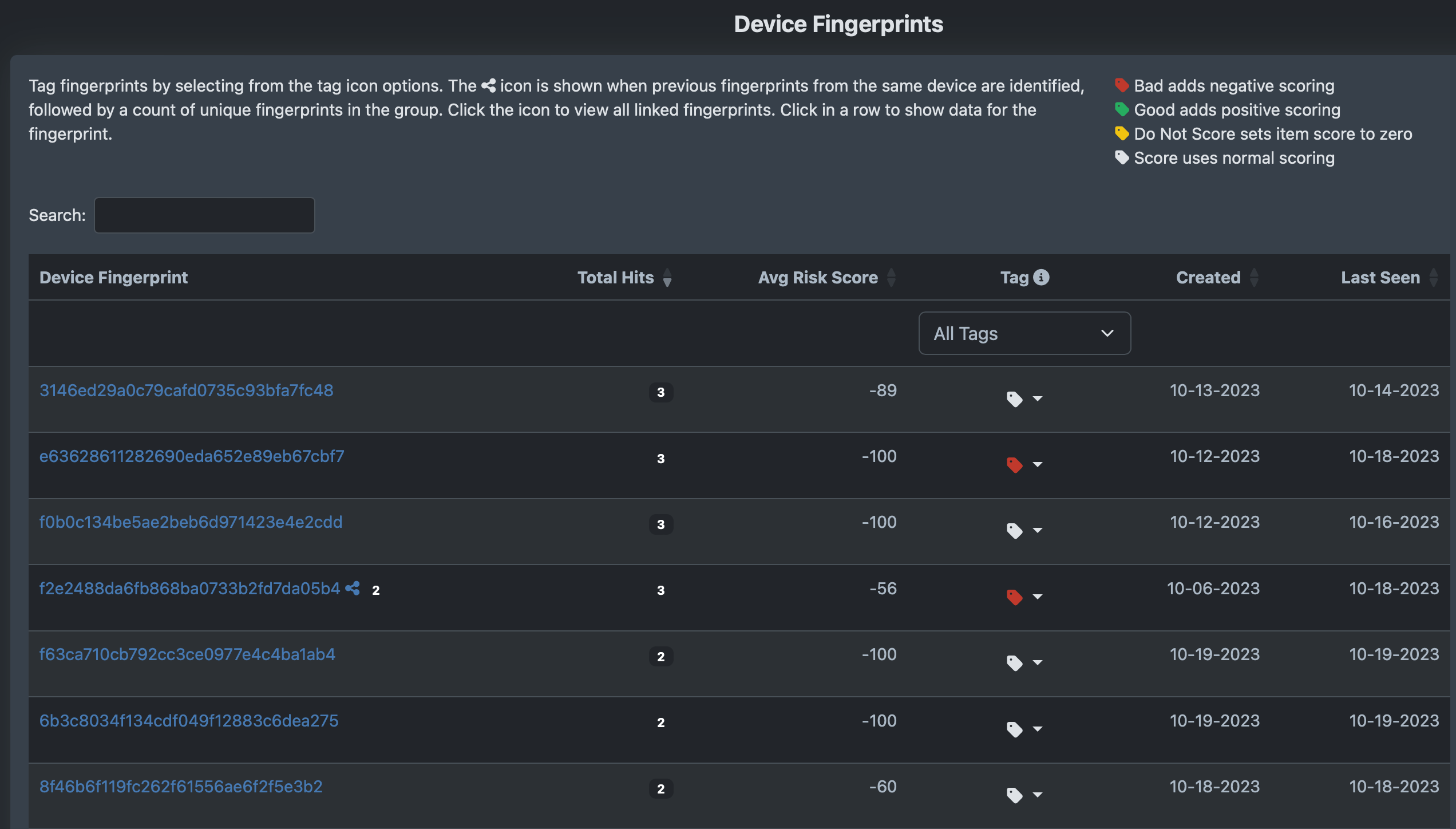
You can tag fingerprints bad, good, do not score or score normally. Fingerprints with a link icon connect previous calls for the same device.
Scoring
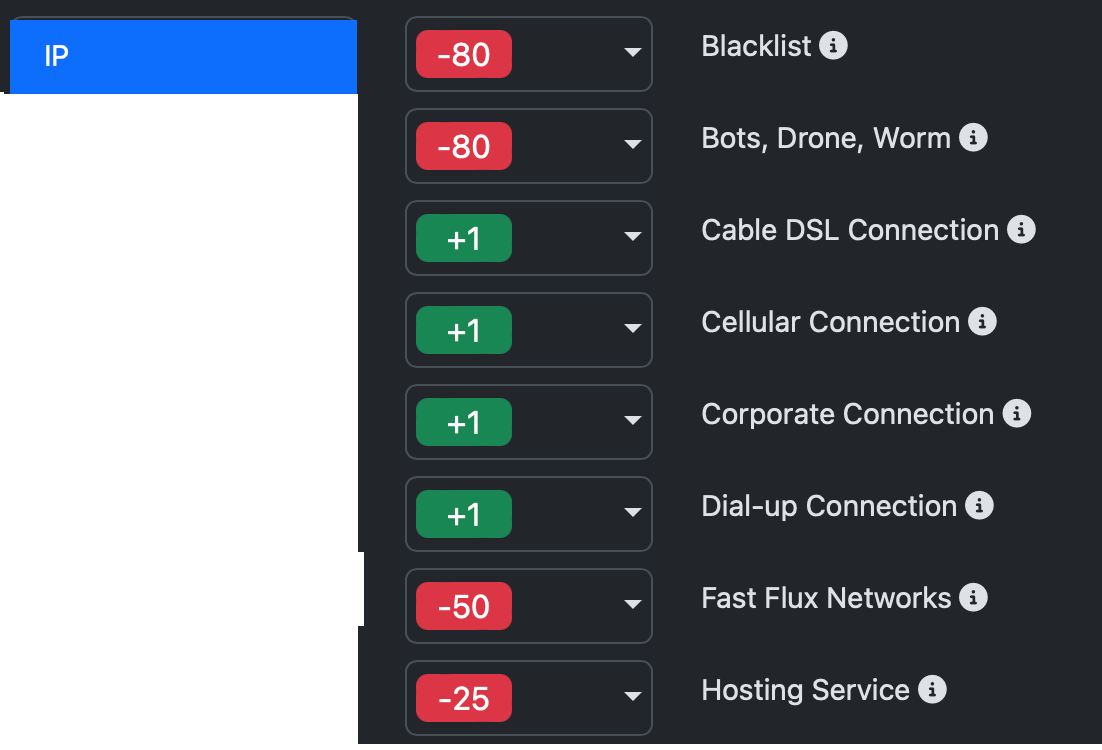
Because each organization views risk differently, risk hit scores are customizable. As an example, tagging a proxy or bot by default results in a High Risk IP score, but you can customize hundreds of these scores to fit your business risk profile using Configure Scores in the Portal.
Tagging
In addition to custom scoring, tagging is used to score specific emails, emaildomains, domains, names, IPs, country codes, device fingerprints, etc. as good, bad, or to skip scoring. Items you tag as Bad will add negative scoring to the risk area. Good tags add positive scoring, and Do Not Score will set the item score to zero. Good and Bad scoring is in addition to standard area scoring. Tags are used to create your private allow, block, and do-not-score lists. Tags can be managed in the Portal or with the Tag API.
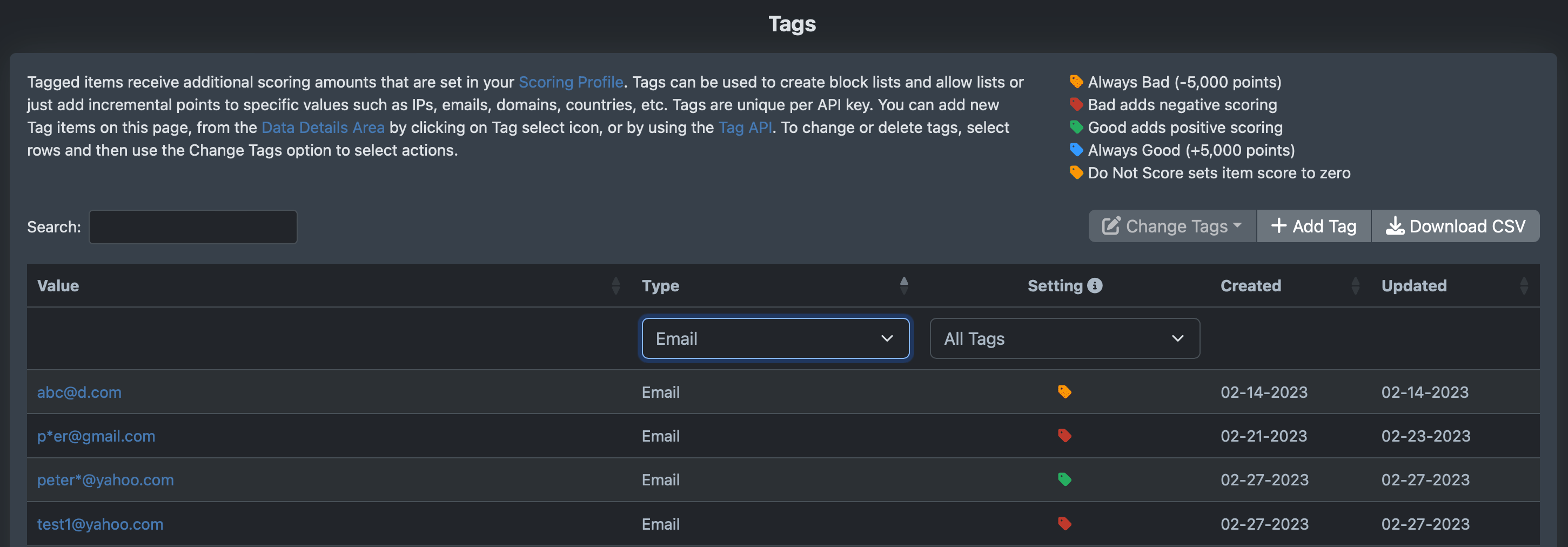
To illustrate how tagging works, if you vet IP = 10.1.1.1, the vet will hit "Private or no geo IP" risk and score -10 for IP area. Adding tags of:
Bad will add -130 to the IP score area, and the IP will now score -140
Good will add +130 to the IP scoring area, and the IP will now score +120
Do Not Score will set the IP scoring to 0
Always Score Good will add 5,000 points and the total score will always be 100 or greater
Always Score Bad will subtract 5,000 points and the total score will always be -100 or less
Activity
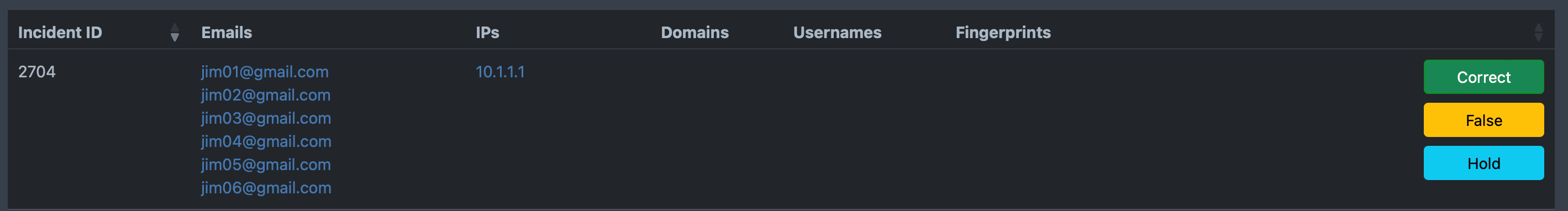
Using phonetic algorithms, pattern matching, and machine learning, the API detects frequency and velocity abuse patterns. This helps eliminate repeat signups, bots, and other fraudsters.
The Portal lists all incidents created by the activity monitor during the last thirty days. To the right of each incident are buttons: Correct to verify the incident as a Repeat Sign-up, False to mark as incorrect (remove from scoring) and Hold to not score until marked correct or false. This report should be checked often because many times the first items in the incident are marked as low risk (no bad pattern yet), and the later ones are marked as high risk. If the incident is Correct, then make sure to take action on all items in the incident.
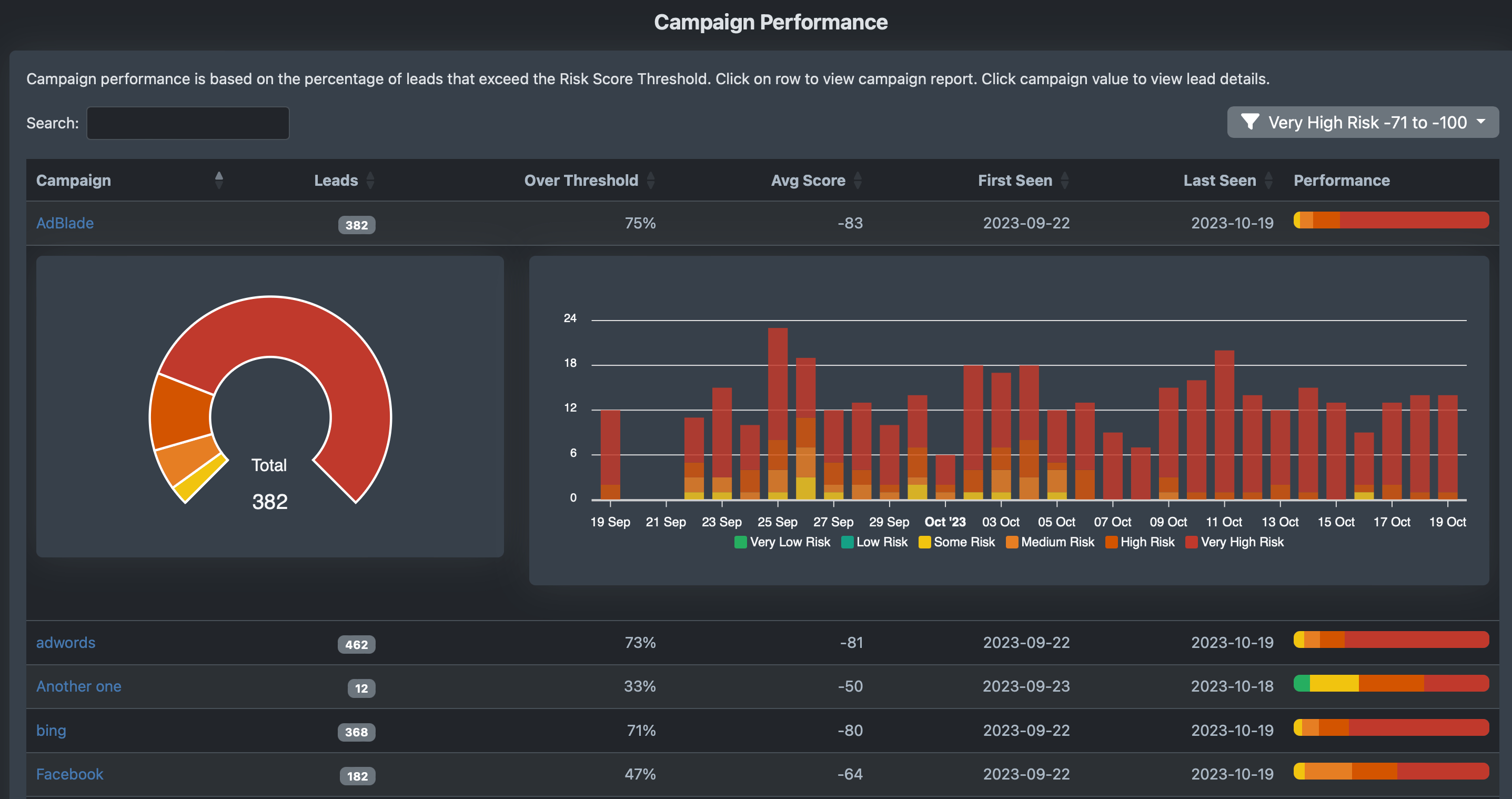
Leads Sources and Campaigns
The service tracks campaign and lead source performance, so you know which ones are delivering the best results. Stop buying leads from sources who deliver bad prospects and optimize campaign conversion rates.
Technology
Our proprietary data includes over fifteen years of historic monitoring from honey-pots, spam traps, phishing monitors, domain reputation as well as real-time feeds of proxy, IP, emails, and pooled data from clients. The data is analyzed using phonetic activity, machine learning algorithms, and correlation tests to tag high risk users quickly.
We track millions of proxies, domains, and device fingerprints, as well as process billions of emails to find IPs, emails, and domains associated with fraud, phishing, cyber crime and spam. Our internal blocklists are supplemented with live feeds from industry leaders, and many of our clients add their fraudsters in real-time to help protect others from attacks. Our platform delivers a thorough risk evaluation tagging individual items of risk (such as proxy, blocklists, disposable email, domain age and parked, invalid phone numbers, and improper locations), followed by phonic algorithms looking for repeat and bot patterns, advanced Geo-correlations including data point mapping and velocity of IPs, phones, locations and device fingerprints, and finally checking against millions of entities and incidents of fraudsters provided by the community.
See also
Reporting and
Analytics
Marketing
Performance
Read
the API documentation